We Need Cloud Transparency Mandates
PLUS: The Hits and Misses in Biden's Cyber Strategy Implementation
Your weekly dose of Seriously Risky Business news is written by Tom Uren, edited by Patrick Gray with help from Catalin Cimpanu. It's supported by the Cyber Initiative at the Hewlett Foundation and this week's edition is brought to you by runZero.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this edition here and on Apple podcasts:

Microsoft and JumpCloud both disclosed breaches of their cloud services last week. It's nice they each disclosed these incidents, but it shouldn't be up to them. We need a mandate that will force cloud service companies to publish detailed postmortems when these things happen.
In the first announcement on 11 July, Microsoft revealed details of a likely China-based actor it calls 'Storm-0558' that had successfully accessed the cloud-based Outlook email of 25 organisations. The actor had targeted government agencies and individual consumer accounts likely associated with these organisations. Microsoft did not specify the affected organisations, but The Washington Post reported that the US Commerce and State departments were affected.
In a more detailed analysis of Storm-0558’s techniques, Microsoft says the group has "primarily targeted US and European diplomatic, economic, and legislative governing bodies, and individuals connected to Taiwan and Uyghur geopolitical interests". According to the vendor, the group’s objective in most campaigns is to access the email accounts of its targets. Microsoft says it has "moderate confidence" that the group is a China-based espionage actor, although from our standpoint, it walks like a duck and quacks like a duck, so it's probably a duck.
According to Microsoft’s report, the group looks pretty competent:
Storm-0558 operates with a high degree of technical tradecraft and operational security. The actors are keenly aware of the target’s environment, logging policies, authentication requirements, policies, and procedures. Storm-0558’s tooling and reconnaissance activity suggests the actor is technically adept, well resourced, and has an in-depth understanding of many authentication techniques and applications.
We find the Storm-0558 attack particularly interesting. First, the actor acquired an inactive Microsoft account (MSA) consumer signing key, a type of key used by Microsoft to sign authentication tokens for its consumer service. (Microsoft is still investigating how this occurred, but security researchers are putting forward theories.)
While this key should only have been able to validate MSA consumer accounts, Storm-0558 took advantage of a flaw in Microsoft's validation process to create tokens that were accepted as valid for enterprise accounts too.
Once it had those tokens, Storm-0558 was able to take advantage of another vulnerability, this time in the Outlook Web Access (OWA) API, to ultimately gain access to mail messages. All in all, clever stuff.
In response to the incident, Microsoft revoked previously active MSA keys and fixed the validation and OWA vulnerabilities. The vendor also says it has "substantially hardened" the systems protecting keys since the key that Storm-0558 used was issued.
Microsoft notes that Storm-0558 historically used phishing campaigns to compromise targets, but has, since at least August 2021, displayed "interest in OAuth applications, token theft, and token replay against Microsoft accounts". It looks like this longer-term interest in authentication tokens paid off in this hack.
Just one day after Microsoft's initial statement on the Storm-0558 incident, JumpCloud announced a state-sponsored group had breached its systems to target some of its customers. JumpCloud did not reveal the actors it believed were responsible, but industry sources told Risky Business News that the Indicators of Compromise JumpCloud released implicate North Korean actors possibly targeting cryptocurrency businesses.
In these incidents JumpCloud and Microsoft say they are publishing information about the incidents because they are committed to transparency.
But we’ve seen the current reliance on voluntary disclosure go wrong before. In the Cloud Hopper campaign, hackers linked to the Chinese Ministry of State Security compromised Managed Service Providers (MSPs). This campaign affected five of the world's 10 biggest service providers, but the scale of the problem was at least partially hidden by the MSPs. According to a Reuters special investigation:
The corporate and government response to the attacks was undermined as service providers withheld information from hacked clients, out of concern over legal liability and bad publicity, records and interviews show. That failure, intelligence officials say, calls into question Western institutions’ ability to share information in the way needed to defend against elaborate cyber invasions. Even now, many victims may not be aware they were hit.
The Cloud Hopper campaign highlights that sometimes the incentive — for both MSPs and cloud service providers — is not to disclose security incidents.
There is also a tendency for cloud providers to deliver services that make it difficult or expensive for clients to do their own security work. In the Storm-0558 compromise of Microsoft services, for example, a US government agency discovered suspicious activity by examining logs from Microsoft's cloud environment (M365) and noticing a change in behaviour — a new AppId was accessing mailboxes. This level of logging requires Microsoft's top tier licence so customers can get ‘Premium’ events.
CISA Director Jen Easterly has taken aim at vendor security price gouging before, saying that full-featured logs should be included in basic product offerings, "rather than as an added, more expensive option". The agency doubled down this week, with a senior official telling reporters on a call that Microsoft's approach "is not yielding the sort of security outcomes that we seek".
In this case, the US government paid extra for the privilege of being able to tell Microsoft that its cloud had been compromised.
Charging extra for these logs is not tenable and Microsoft announced yesterday it was expanding access to more log types at no extra cost, starting from September.
But this is about more than Microsoft and its pricing strategy.
At a micro level the shift to cloud services is redrawing security boundaries and responsibilities between customers and providers. On balance, for most individual cloud service customers, this probably is a good thing. But it should not be left to cloud service providers to decide when to tell customers that things have gone wrong. At the very least, vulnerability and breach disclosures with in-depth post-mortems should be mandatory, not just when providers feel like it.
At a macro level, there is an argument that the shift to the cloud means that instead of reducing absolute risk we are just concentrating it in just a few "hyperscale" vendors. From an individual perspective most customers are likely better off, but overall we are putting more and more eggs into fewer and fewer baskets.
Fundamentally, cloud service providers are well positioned to provide good security services to a lot of organisations en masse. But they shouldn't be left to do so as the market dictates. They need to be held to very high standards.
The Hits and Misses in Biden's Cyber Strategy Implementation
The Biden administration has released its national cyber security strategy implementation plan, building on its overarching March strategy document.
We really like the overall strategy, although our critique at the time was that for the most ambitious and consequential part of the strategy — Shape Market Forces to Drive Security and Resilience — the US government presented a "destination without a roadmap".
This part of the strategy could be transformative by changing how organisations and vendors approach cyber security and develop secure products.
This section of the implementation plan is underdone, particularly the objective to "shift liability for insecure software products and services". The concrete actions listed here are to advance software bills of material, improve coordinated vulnerability disclosure and hold a legal symposium.
By contrast, another key section of the implementation document, 'Disrupt and Dismantle Threat Actors' is chock full of effective initiatives that complement and reinforce each other. These initiatives harness federal government agencies to work with the private sector to improve the speed and scale of disruption operations against cyber threat actors. We think these initiatives will work, so we look forward to many more disruption campaigns.
Operation Typo: Mali in Box Seat to Collect on US Military
The Financial Times has a great story (republished on Ars Technica) about the sustained, albeit somewhat random, collection of emails destined for the US military. The collection opportunity arises because email meant for the US military with its top-level domain ".mil" is instead mistakenly sent to ".ml", the country-code top-level domain for Mali.
The current manager of the .ml domain, Dutch entrepreneur Johannes Zuurbier, has collected over 117,000 misdirected emails since January this year in an effort to convince the US government of the problem.
To make matters worse, on Monday 24 July, the .ml domain will return to the control of Mali's government, which is closely allied with Russia.
Internally, the US military has technical controls in place to prevent the inadvertent sending of emails to .ml addresses, but the problem arises when people do not use .mil systems. This commonly includes travel agents and staff who send emails to their work accounts.
Although the emails are unclassified and many are spam, the aggregation of so much email destined for the US military could be significant. Some of the pieces Zuurbier has intercepted are positively hair-raising. The Financial Times article says:
But some messages contain highly sensitive data on serving US military personnel, contractors, and their families.
Their contents include X-rays and medical data, identity document information, crew lists for ships, staff lists at bases, maps of installations, photos of bases, naval inspection reports, contracts, criminal complaints against personnel, internal investigations into bullying, official travel itineraries, bookings, and tax and financial records…
One misdirected email this year included the travel plans for General James McConville, the chief of staff of the US Army, and his delegation for a then-forthcoming visit to Indonesia in May.
The email included a full list of room numbers, the itinerary for McConville and 20 others, as well as details of the collection of McConville’s room key at the Grand Hyatt Jakarta, where he received a VIP upgrade to a grand suite.
Zuurbier has approached US officials repeatedly, without satisfaction. A Pentagon spokesman, Lt. Cmdr Tim Gorman gave the Financial Times a nothingburger response, saying the Department of Defense "is aware of this issue and takes all unauthorised disclosures of controlled national security information or controlled unclassified information seriously".
This seems like a classic bureaucratic problem that festers because it doesn't fit into any US DoD job description. Our advice here is that someone should just work up the gumption to jump through the policy hoops and hurdles and buy the relevant .ml domains. Dealing with the bureaucracy will be extremely painful, but hopefully Mali's government won't charge too much.
Three Reasons to Be Cheerful this Week:
FCC plans to fund school cyber security upgrades: The US Federal Communications Commission plans to allow K-12 schools and libraries to use funds from its E-Rate program to improve cyber security. Dating back to 1996, E-Rate can be used to purchase discounted internet subscriptions and networking devices.
US sanctions spyware vendors: The Biden administration has put Intellexa and Cytrox on the federal entity list, which prohibits US companies from doing business with the firms. Sanctions against NSO Group look to have been pretty effective, so we approve.
CISA's cloud security tools: the US Cybersecurity and Infrastructure Security Agency has brought its collection of cloud security tools into a single page.
Sponsor Section
RunZero is one of this newsletter's main supporters and this week's featured sponsor. The company's main product is its network discovery and asset inventory platform, which can be used to find any managed and unmanaged assets inside a customer's network, including OT devices in critical environments. To learn more, please check out this runZero product demo below:
Shorts
Snitching on Drug Deals Is Not Breaking E2EE
A US Senate bill aims to force internet communications companies to report illicit drug-related activity on their platforms to the Drug Enforcement Administration. It has been described as a potential challenge to end-to-end encryption (E2EE), but we don't think so.
While the Bill requires companies to report to the DEA what they know of drug crimes, it does not require them to monitor or scan messages, "so long as the provider does not deliberately bind itself to those violations". What does that even mean? Removing E2EE without scanning messages won't achieve much, so it's hard to know what this language in the Bill is actually aiming for.
Now Made in China: Stealthy Cyber Espionage
Mandiant has examined the techniques Chinese cyber espionage groups are using to avoid detection and complicate attribution. When it comes to gaining access, the focus on exploiting networking, security and virtualisation technologies has a number of advantages. These devices are located at network edges, and there's often no EDR.
When it comes to command and control, they obfuscate traffic using botnets of compromised IoT devices or routers. They also tunnel traffic within networks to avoid detection.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq look at the idea of actively shaping ransomware group behaviour to get the crimes we’d prefer.
From Risky Biz News:
IoT cybersecurity labelling scheme coming to the US in 2024: The White House and the FCC have announced a voluntary cybersecurity labelling program for internet-connected devices sold in the US.
The program will roll out in 2024 and is named the US Cyber Trust Mark.
It will take the form of a shield logo applied to routers and IoT devices sold through US retailers. The logo will be applied to devices that meet a set of basic cybersecurity criteria, such as devices using unique and strong default passwords, can receive security updates, protect user data, and restrict access to their management interfaces.
[more on Risky Business News]
Multichain cyber-heist, part 2: An additional USD$103 million in crypto-assets have been moved out of the accounts of the Multichain cryptocurrency exchange. The new transfers come after an initial batch of $126 million was mysteriously moved from the company's accounts over the past weekend. The company has not provided any updates after the initial transfers. Many of its users fear the company was either hacked or its staff is executing a rug pull and running away with their funds. [Additional coverage in Decrypt]
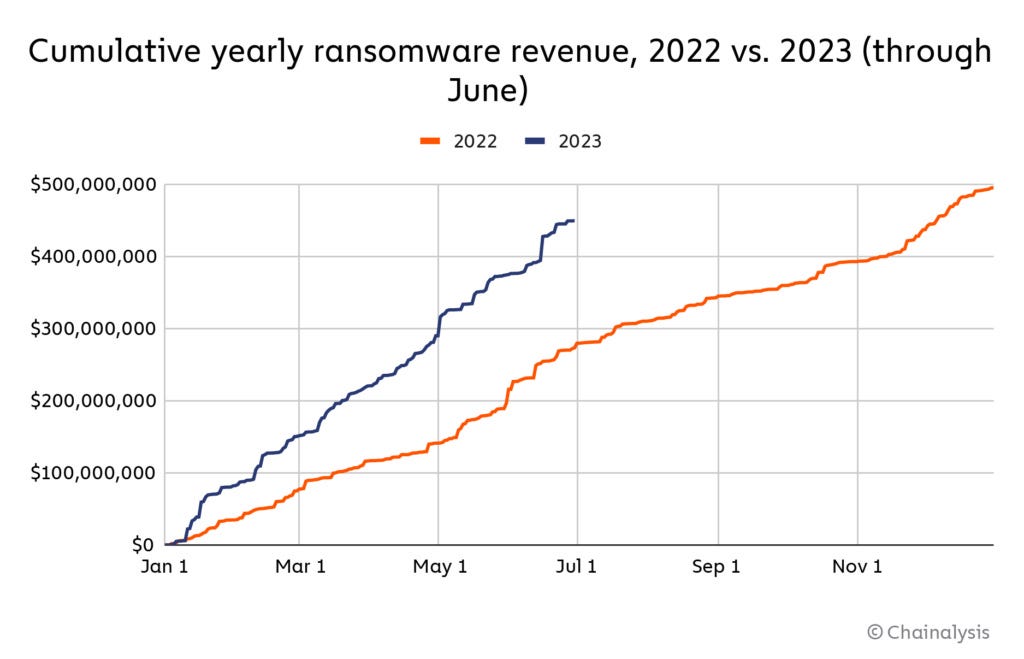
Ransomware returns: Ransomware gangs have extorted at least $450 million from victims in the first half of the year, a figure that shows the slump ransomware gangs experienced after Russia's invasion of Ukraine is now over. Blockchain analytics company Chainalysis expects groups to make $890 million by the end of 2023, which will give ransomware gangs their second most profitable year on record. Their most successful year was 2021—when they extorted around $940 million from victims.