Microsoft Should Look to the Past for Its Security Future
PLUS: EncroChat Interception Cut Short by Police Leak
Your weekly dose of Seriously Risky Business news is written by Tom Uren and edited by Patrick Gray. It's supported by Lawfare and this week's edition is brought to you by runZero.
You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business News" in your podcatcher or subscribing via this RSS feed. Find this edition here and on Apple podcasts:
Last week, Microsoft announced a “Secure Future Initiative" to improve its ability to cope with increasingly sophisticated cyber security threats.
This reminds us of Microsoft's last security epiphany, the Trustworthy Computing initiative, launched in 2002. Unfortunately, compared to the clarity, focus and commitment of the Trustworthy Computing initiative, this announcement is disappointing.
In a post describing the Secure Future Initiative, Microsoft President and Vice Chair Brad Smith wrote that the new initiative was required because of the "increasing speed, scale and sophistication of cyberattacks".
We don't think Smith is quite right here. We would say Microsoft needs security reform because it has been making unacceptably vulnerable products.
Threats are increasing in speed, scale and sophistication, but the fundamental problem for Microsoft is that its security culture just isn't up to scratch. In a breach of its email services earlier this year, for example, Microsoft's own post-mortem revealed a series of decision-making failures that simply would not have occurred in a security-conscious organisation.
This results in products that are not as secure as they should be. This newsletter has covered a constant flow of Microsoft security gaffes over the past few years.
These security flaws draw in attackers like flies to rotting meat.
Smith wrote that Microsoft's efforts will consist of three pillars "focused on AI-based cyber defences, advances in fundamental software engineering, and advocacy for stronger application of international norms to protect civilians from cyber threats".
The most promising part of the initiative describes specific engineering goals that Microsoft is committing to. Charlie Bell, Microsoft’s Security Vice President, expands on these in an internal email, where he writes that Microsoft will:
"transform the way we develop software with automation and AI so that we do our best work in delivering software that is secure by design, by default, in deployment, and in operation"
"provide a unified and consistent way of managing and verifying the identities and access rights of our users, devices, and services, across all our products and platforms"
Improve the speed of vulnerability response and security updates on cloud platforms to "cut the time it takes to mitigate cloud vulnerabilities by 50 percent".
This all sounds good, and we cover some positive initiatives in Three Reasons to be Cheerful this week. But overall, we are terribly underwhelmed by Microsoft's messaging here. In his email Bell issues a lukewarm call to arms:
We recognise that not all of you will be deeply involved in all of the advances we must make. After all, the first priority is security by default. But all of you will be engaged and, more importantly, your constant attention to security in everything you build and operate will be the source of continuous innovation for our collective secure future. Please read on, absorb the "what" and the "why," and contribute your ideas on innovation. We are all security engineers.
In 2001, Microsoft was at a similar crossroads after it had been stung by a series of security problems, including the CodeRed and Nimda worms. In January 2002 Bill Gates sent an internal email that launched Microsoft's Trustworthy Computing initiative. In his very first paragraph Gates is crystal clear that the initiative is the top priority for everyone in the company:
Over the last year it has become clear that ensuring .NET (Ed: a new Microsoft computing platform at the time) is a platform for Trustworthy Computing is more important than any other part of our work. If we don’t do this, people simply won’t be willing — or able — to take advantage of all the other great work we do. Trustworthy Computing is the highest priority for all the work we are doing. We must lead the industry to a whole new level of Trustworthiness in computing.
Towards the end of his email Gates re-emphasised the importance of Trustworthy Computing and underscored how Microsoft needed to shift its priorities:
In the past, we’ve made our software and services more compelling for users by adding new features and functionality, and by making our platform richly extensible. We’ve done a terrific job at that, but all those great features won’t matter unless customers trust our software. So now, when we face a choice between adding features and resolving security issues, we need to choose security. Our products should emphasise security right out of the box, and we must constantly refine and improve that security as threats evolve… If we discover a risk that a feature could compromise someone’s privacy, that problem gets solved first. If there is any way we can better protect important data and minimise downtime, we should focus on this. These principles should apply at every stage of the development cycle of every kind of software we create, from operating systems and desktop applications to global Web services.
This single paragraph clearly spells out how Microsoft went wrong, why it needed to change and what its new priorities were. After this memo Microsoft's security really did improve, for a while.
By contrast, Smith and Bell's messages about the Secure Future Initiative make no mention of changed priorities and what Microsoft will forego to achieve better security. Is the expectation that security improvements will flow naturally from doing extra engineering work rather than requiring any recalibration of Microsoft's priorities?
Beyond these engineering efforts, a large section of Smith's post deals with how Microsoft will use AI to improve security. Within Microsoft, the company will use it to improve its threat intelligence and cope with a "vast sea of digital data" including by helping it to "to find the right needle even in a sea of needles".
Outside the organisation Microsoft will use AI "as a gamechanger for all organisations to help defeat cyberattacks at machine speed". Of course, using AI responsibly is also a must.
I mean, I guess this is good, but how much of your security strategy should rely on AI being a game changer? Will the technology super charge Microsoft's security? Or just make security professionals moderately more effective? In our view, exploring AI to improve cyber security is a worthwhile experiment, but it is no substitute for the commitment to security that Gates demonstrated in 2002.
Smith's post finishes with norms of international behaviour, which he describes as a "third critical component" of Microsoft's Secure Future Initiative. This commits Microsoft to advocate for standards that would govern the behaviour of actors in cyberspace, including both government and non-state actors.
This section contains a diverse mix of recommendations or commitments that range from the sensible to the naive and sometimes self-serving. For example, "states should recognise cloud services as critical infrastructure, with protection against attack under international law".
We don’t think pursuing changes to international standards or behaviours will change the way threat actors behave in any significant way. Microsoft should focus on the baseline security of its products, with lobbying for better behaviour from states and cybercriminals a second- or third-order issue.
Fundamentally, our critique of the Secure Future Initiative stems from our diagnosis that Microsoft isn't delivering secure products because its culture does not value security appropriately. It won't fix that problematic culture by launching engineering efforts, using AI, or by improving international norms of behaviour.
Encrochat Crimephone Operation Cut Short By Police Leak
Natalie Mottram, a former intelligence analyst for the Cheshire Police, has been jailed in the UK for revealing to criminals that the EncroChat encrypted crimephone had been hacked by law enforcement agencies.
The EncroChat system was breached by a French interception operation in April 2020. That month, Mottram told Jonathan Kay, her friend and flatmate and a man with criminal connections, that EncroChat had been compromised. Associates of Kay used EncroChat to warn other users that the system had been compromised and by June the company EncroChat shut it down after learning it had been breached.
The UK's National Crime Agency learnt there was a leak when they intercepted some of these messages warning of a breach. The NCA then launched a sting operation to confirm Mottram was responsible.
The police action against EncroChat was tremendously successful and here is more on the history of police actions against crimephones.
Three Reasons to Be Cheerful This Week:
More, Better MFA for all: Microsoft has announced that it will automatically roll out conditional access policies to Microsoft Entra ID (formerly Azure Active Directory) customers. This means that more users will be required to use multi-factor authentication and Microsoft's goal is to have 100% MFA authentication. Microsoft has also rolled out a feature to combat MFA push fatigue attacks where suspicious or risky login attempts won't result in a notification on a user's phone. Instead users will be prompted to open Microsoft's Authenticator app to complete the sign-in process.
Indian crypto-scam arrests: Indian authorities arrested eight people, including four police, involved in crypto-related scams. This is part of a continuing crackdown with 18 people arrested so far.
Dodgy VPNs need not apply: The Google Play store has started to add security audit badges to VPN apps. An app can earn these badges by undergoing an independent security check through an approved partner. Bleeping Computer has good coverage.
Sponsor Section
In this Risky Business News sponsor interview, Tom Uren talks to Huxley Barbee, Security Evangelist at runZero, about finding the unknown unknowns and what is a security evangelist.
Sponsor Demo
Senior Sales Engineer Ali Cheikh demonstrates the runZero platform to Risky Business host Patrick Gray. runZero is a cyber asset management tool that combines active scanning, passive discovery, and API integrations to discover IT, OT, and IoT assets (both managed and unmanaged) across your network, including cloud, mobile, and remote environments.
Shorts
eIDAS Is Just a Terrible Idea
More than 300 companies, NGOs, scientists and researchers have asked the EU to reconsider its proposed eIDAS regulation (Electronic Identification, Authentication and Trust Services) in two separate open letters.
Both the industry joint statement and the letter from civil society organisations and individuals argue that the regulation would undermine web security. The regulation proposes that any EU member government be able to issue certificates that web browsers must accept as valid, which would potentially allow any EU member state to intercept the web traffic of any EU citizen, for example. The industry letter was signed by Cloudflare, Akamai and Mozilla, and Google also separately backed this industry position. The Record has further coverage.
Iran-Israel Cyber Argy Bargy
According to Palo Alto Networks, an Iranian-backed hacking group that it calls Agonizing Serpens, has launched a series of destructive attacks targeting the education and technology sector in Israel from January through October this year. Microsoft has linked the group, also known as Agrius, Pink Sandstorm, and BlackShadow, to Iran's Ministry of Intelligence and Security.
Russia Arrests Cybercriminals When It Wants To
Risky Business News reports that the Russian FSB detained two men accused of attacking Russian IT systems on behalf of Ukraine:
Officials detained a student from Tomsk and a 36-year-old from Belovo, Kemerovo. The FSB says the two suspects joined Ukraine's "cyber troops," received orders from Ukraine's security services, and attacked Russian critical infrastructure. The two have been charged with high treason and face prison sentences from 12 years to life in prison.
There are two lessons here. Firstly Russia has some capacity to arrest cyber criminals when the government cares. Secondly, attacking Russian IT systems from within the country is just a bad idea.
Risky Biz Talks
You can find the audio edition of this newsletter and other fine podcasts and interviews in the Risky Biz News feed (RSS, iTunes or Spotify).
In our last "Between Two Nerds" discussion Tom Uren and The Grugq discuss the 35th anniversary of the Morris worm and what it tells us about the evolution of cyber security.
From Risky Biz News:
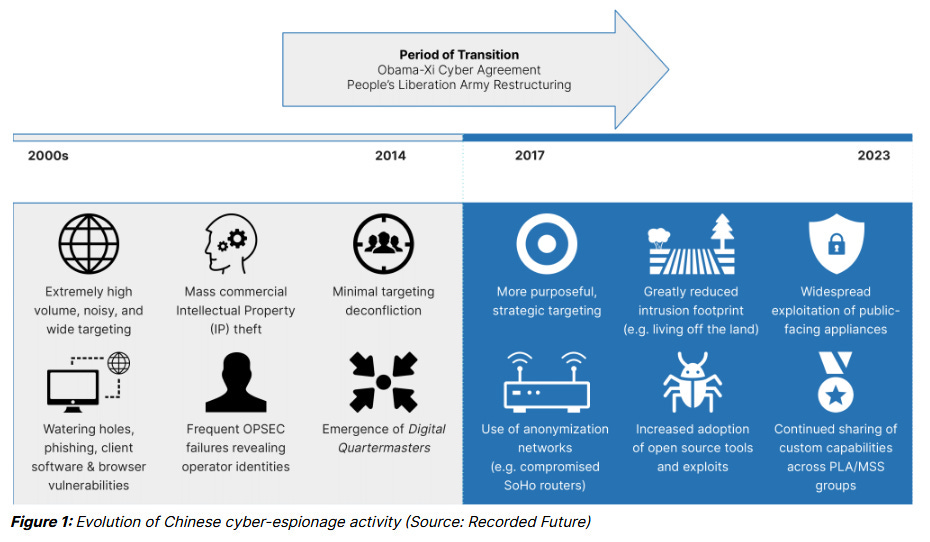
Chinese APTs evolve towards stealth, zero-day abuse: Chinese state-sponsored hacking operations have undergone a major shift in recent years, with groups growing in sophistication and abandoning noisy and high-volume campaigns for stealthy and extremely targeted attacks…
Recorded Future published an excellent report this week that perfectly contextualises what has been happening with China's APTs in the 2020s.
[much more on Risky Business News, including trends such as the move away from custom malware and adoption of living-off-the-land techniques, and shifting from high-volume targeting towards "more coordinated and thoughtful" targeting.]
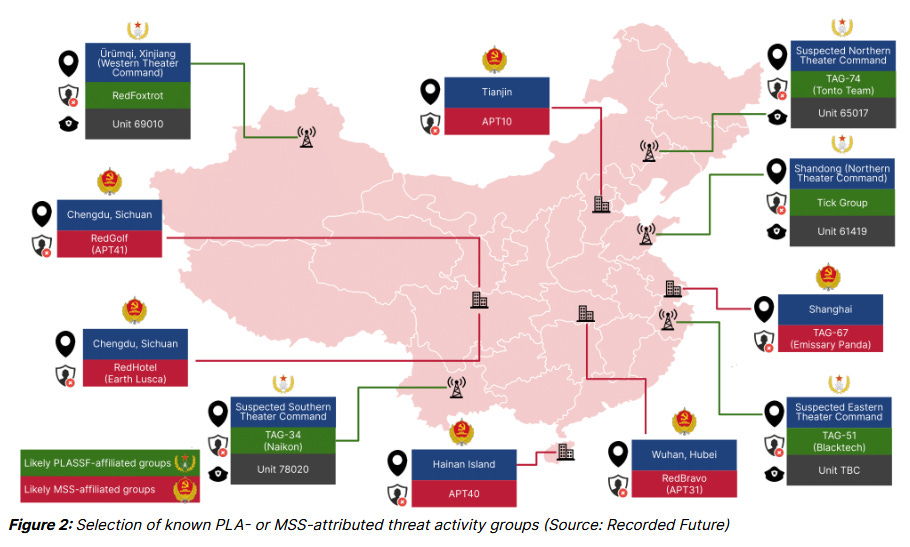
Finally, the report also includes an attribution map for China's APT groups, including their suspected geographical locations. This is in line with what Sekoia published earlier this year, too.
US sanctions Russian woman for laundering money for Ryuk gang, Russian elites: The US Treasury has sanctioned a Russian businesswoman named Ekaterina Zhdanova for helping Russian oligarchs and cybercrime gangs evade sanctions and launder stolen cryptocurrency.
Officials say Zhdanova operated a luxury watch company with offices around the world in order to maintain access to the global financial system. She was also a customer of Garantex, a Russian cryptocurrency exchange the Treasury sanctioned in April 2022 for laundering more than $100 million in cybercrime proceeds.
According to US officials, Zhdanova was involved in laundering more than $105 million for her customers.
Mozi botnet goes down: The Mozi botnet has finally gone down for good after a mysterious entity removed its malware from infected IoT devices across the globe. The removal took place at the end of August, with infected hosts being first removed from systems in India and then from China. Security firm ESET says the Mozi takedown was executed with a special killswitch component that was signed with the malware's original private key. The company couldn't say if the killswitch was activated by the Mozi botnet creators or by Chinese law enforcement, which detained some of the Mozi authors in June 2021. First spotted in November 2019, the botnet infected more than 1.5 million devices across its lifetime, peaking at 160,000 infected systems in September 2020.